Securing a Django site at the perimeter
Sometimes contrib.auth just isn't enough
We run a number of working environments on Heroku - in addition to the live site we have dedicated UAT and DEV environments, a DEMO environment for the sales team, and since the recent Heroku pricing changes we're thinking about a spinning up a new environment per developer (so they can push feature branches to a public location for review).
This all works well, but it does mean we have a very large surface area of work that we'd rather not make public. In practice, the only part of our site that is genuinely public is the homepage, so this is not really an issue, but it would still be helpful to be able to restrict public access to these sites outside of the application auth system. e.g. at the perimeter.
We couldn't find anything we could use out of the box, and because we run on Heroku we can't do anything with Nginx / Apache configurations (and we don't want to be editing conf files to do this), so we built our own - say hello to django-perimeter.
It's pretty simple - it runs as middleware, and prevents anything getting in to the site without a valid access token. The tokens are managed through the Django admin site, or by a management command. When enabled, users will see this on first visit:
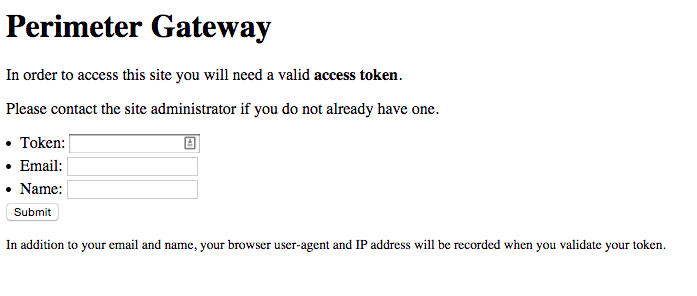
Once they've submitted a valid token, they get the full run of site.
Check it out (it's on Github), fork it, improve it, send pull requests...
Making Freelance Work
Posted in: django
